Owasp top 10 vulnerabilities 2013 pdf Preeceville

Web Application (OWASP Top 10) Scan Report SAINT Threat Prevention Coverage – OWASP Top 10 Analysis of Check Point Coverage for OWASP Top 10 Website Vulnerability Classes The Open Web Application Security Project (OWASP) is a worldwide not-for-profit charitable organization focused on
OWASP TOP 10 2013 ~ compliance report Gold Security
OWASP postpones publication of Top 10 app vulnerabilities. What are these risks? You can find them in the OWASP Top 10 list. Image Credit: Helga Weber via photopin cc . 4 The 10 Biggest Application Security Risks (OWASP Top 10) The Open Web Application Security Project (OWASP) is a highly -respected online community dedicated to web application security. Their ^OWASP Top Ten _ list outlines the biggest security vulnerabilities facing modern …, The OWASP Foundation typically publishes a list of the top 10 security threats on an annual basis (2017 being an exception where RC1 was rejected and revised based on inputs from market experts.
Just to mention, at least since 2010 this is the most prevalent vulnerability class in web applications that lead to RCE in PHP environments and since 2013 in Java. But anyway, I stopped paying attention to OWASP TOP 10 years ago. 2/02/2015В В· Sensitive Data Exposure is currently ranked #6 on the OWASP Top 10 chart. If your web applications do not properly protect sensitive data, such as credit car...
OWASP Top 10 Presents the 10 most critical web application security risks Produced by the Open Web Application Security Project (OWASP) Available on line www.owasp.org Updated in 2013 Not Exhaustive hundreds of other issues occure in Web Security But it is foccused on the most critical ones Berner Fachhochschule j Haute cole spcialise bernoise j Berne University of Applied Sciences 10. OWASP Our OWASP TOP 10 posts offer an insight into each of the 10 vulnerability types on OWASP’s list. We describe the vulnerabilities, the impact they can have, and highlight well-known examples of events involving them. Of course, we also explain how to discover these vulnerabilities, providing code
20/11/2018В В· On June 12, 2013 the OWASP Top 10 for 2013 was officially released. This version was updated based on numerous comments received during the comment period after the release candidate was released in Feb. 2013. This open-source tool was developed at the Open Web Application Security Project (OWASP). Its main goal is to allow easy penetration testing to find vulnerabilities in web applications. It is ideal for developers and functional testers as well as security experts.
Welcome Welcome to the OWASP Top 10 2013! This update broadens one of categories from the 2010 version to be more inclusive of common, important vulnerabilities, and reorders some of the others based on changing prevalence data. 21/08/2015 · Please visit the OWASP Top 10 project page to find the latest edition. ← Risk: 2013 Table of Contents. 2013 Top 10 List. A1-Injection → A1-Injection Injection flaws, such as SQL, OS, and LDAP injection occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing
OWASP Top 10 Security Vulnerabilities 2013 This paper addresses security vulnerabilities documented by the OWASP for the year 20132. Lucky enough, the OWASP Top 10 list for the year 2013 doesn’t differ much from lists published for previous years, except for changes in ranking. The listed security threats are probably the most severe threats and application developers to be aware of … Our OWASP TOP 10 posts offer an insight into each of the 10 vulnerability types on OWASP’s list. We describe the vulnerabilities, the impact they can have, and highlight well-known examples of events involving them. Of course, we also explain how to discover these vulnerabilities, providing code
As application security threats are constantly evolving, the current OWASP Top 10 is the 2017. This list includes detailed best practices for both the detection and remediation of vulnerabilities. Building on the success of the original OWASP Top Ten for web applications, OWASP has produced further 25/11/2014 · This vulnerability category is currently ranked #2 on the OWASP Top 10 chart and is very commonly exploited. These types of weaknesses …
OWASP Top Ten: The "Top Ten", first published in 2003, is regularly updated. It aims to raise awareness about application security by identifying some of the most critical risks facing organizations. As application security threats are constantly evolving, the current OWASP Top 10 is the 2017. This list includes detailed best practices for both the detection and remediation of vulnerabilities. Building on the success of the original OWASP Top Ten for web applications, OWASP has produced further
OWASP is a volunteer organization that’s become a mainstay of the cybersecurity community, and their Top 10 list of app vulnerability categories is the most downloaded document on their website, the organization says. An Overview of the 2013 OWASP Top 10 By Mike Sheward Lists are all over the Internet. Just yesterday I found myself wasting 12 minutes of my life reviewing вЂthe 7 …
•OWASP Top 10 is a list of the most risky web app vulnerabilities •Test the devices and services against OWASP Top 10 to establish a common baseline •Low resources in the devices are not an excuse for not showing due care in security When it comes to OWASP Top 10 vulnerabilities and best practices for web applications, the riskiest and most successful exploits in terms of valuable data …
Browsable web directory. A web directory was found to be browsable, which means that anyone can see the contents of the directory. Browsable directories could allow an attacker to view “hidden” files in the web root, including CGI scripts, data files, or backup pages. •OWASP Top 10 is a list of the most risky web app vulnerabilities •Test the devices and services against OWASP Top 10 to establish a common baseline •Low resources in the devices are not an excuse for not showing due care in security
Web Application (OWASP Top 10) Scan Report SAINT. An Overview of the 2013 OWASP Top 10 By Mike Sheward Lists are all over the Internet. Just yesterday I found myself wasting 12 minutes of my life reviewing вЂthe 7 …, When it comes to OWASP Top 10 vulnerabilities and best practices for web applications, the riskiest and most successful exploits in terms of valuable data ….
OWASP Top 10 checkmarx.com

OWASP 2017 Top 10 vs. 2013 Top 10 InfoSec Resources. 2/02/2015В В· Sensitive Data Exposure is currently ranked #6 on the OWASP Top 10 chart. If your web applications do not properly protect sensitive data, such as credit car..., 20/11/2018В В· On June 12, 2013 the OWASP Top 10 for 2013 was officially released. This version was updated based on numerous comments received during the comment period after the release candidate was released in Feb. 2013..
OWASP TOP 10 2013 ~ compliance report Gold Security. 2/02/2015 · Sensitive Data Exposure is currently ranked #6 on the OWASP Top 10 chart. If your web applications do not properly protect sensitive data, such as credit car..., 25/11/2014 · This vulnerability category is currently ranked #2 on the OWASP Top 10 chart and is very commonly exploited. These types of weaknesses ….
OWASP Top 10 checkmarx.com

2013 OWASP Top 10 Most Dangerous Port80 Software. Let's take run through the OWASP TOP 10 to remind ourselves of how we can better protect our applications, our businesses, and our customers from unlawful and damaging cyber attacks which could be prevented by implementing the correct procedures in the right places. https://cs.wikipedia.org/wiki/OWASP Top 10 2013.pdf.Every three years the Open Source Web Application Consortium releases its list of the top 10 web vulnerabilities. Year after year, top threats like SQL injection.May 29, 2011..
OWASP Top 10 Presents the 10 most critical web application security risks Produced by the Open Web Application Security Project (OWASP) Available on line www.owasp.org Updated in 2013 Not Exhaustive hundreds of other issues occure in Web Security But it is foccused on the most critical ones Berner Fachhochschule j Haute cole spcialise bernoise j Berne University of Applied Sciences 10. OWASP In 2013 OWASP completed its most recent regular three-year revision of the OWASP Top 10 Web Application Security Risks. The Top Ten list has been an important contributor to secure application development since 2004, and was further enshrined after it was included by reference in the in the Payment Card Industry Security Standards Council’s Data Security Standards, better known as the …
This open-source tool was developed at the Open Web Application Security Project (OWASP). Its main goal is to allow easy penetration testing to find vulnerabilities in web applications. It is ideal for developers and functional testers as well as security experts. Top 10 2013.pdf.Every three years the Open Source Web Application Consortium releases its list of the top 10 web vulnerabilities. Year after year, top threats like SQL injection.May 29, 2011.
An Overview of the 2013 OWASP Top 10 By Mike Sheward Lists are all over the Internet. Just yesterday I found myself wasting 12 minutes of my life reviewing вЂthe 7 … This open-source tool was developed at the Open Web Application Security Project (OWASP). Its main goal is to allow easy penetration testing to find vulnerabilities in web applications. It is ideal for developers and functional testers as well as security experts.
The OWASP Top 10 Project (OWASP, 2012), which assesses the most critical threat categories against web applications, places Г”Unvalidated InputГ• in the top spot, follow ed by the related XSS Flaws and Welcome Welcome to the OWASP Top 10 2013! This update broadens one of categories from the 2010 version to be more inclusive of common, important vulnerabilities, and reorders some of the others based on changing prevalence data.
OWASP top ten security vulnerabilities 2013. To guide developers for what they need to protect against, the Open Web Application Security Project publishes an annual document that lists the ten most critical security vulnerabilities identified for a year. In 2013 OWASP completed its most recent regular three-year revision of the OWASP Top 10 Web Application Security Risks. The Top Ten list has been an important contributor to secure application development since 2004, and was further enshrined after it was included by reference in the in the Payment Card Industry Security Standards Council’s Data Security Standards, better known as the …
2/02/2015 · Sensitive Data Exposure is currently ranked #6 on the OWASP Top 10 chart. If your web applications do not properly protect sensitive data, such as credit car... The 2013 OWASP Top 10 release candidate is out and available for comment now. Since the list’s inception in 2004 much has changed online, and much has stayed the same. Many of the vulnerabilities from the original top ten have been on every list since or …
OWASP top 10 is the list of top 10 application vulnerabilities along with the risk, impact, and countermeasures. The list is usually refreshed in every 3-4 years. The list is … OWASP Top 10 Vulnerabilities. Preview. Start a free Basic trial to watch this video. Sign up for Treehouse . CSRF 7:44 with Jared Smith. A CSRF attack forces a logged-on victim’s browser to send a forged HTTP request, including the victim’s session cookie and any other automatically included authentication information, to a vulnerable web application. This allows the attacker to force the
•OWASP Top 10 is a list of the most risky web app vulnerabilities •Test the devices and services against OWASP Top 10 to establish a common baseline •Low resources in the devices are not an excuse for not showing due care in security The OWASP Top 10 Project (OWASP, 2012), which assesses the most critical threat categories against web applications, places ÔUnvalidated InputÕ in the top spot, follow ed by the related XSS Flaws and
shaddygarg [9:02 AM] uploaded and commented on this image: OWASP.PNG. The vulnerabilities A7, A9, A8 are merged into some other vulnerabilities of 2013 and other vulnerabilities are the same. Threat Prevention Coverage – OWASP Top 10 Analysis of Check Point Coverage for OWASP Top 10 Website Vulnerability Classes The Open Web Application Security Project (OWASP) is a worldwide not-for-profit charitable organization focused on
As application security threats are constantly evolving, the current OWASP Top 10 is the 2017. This list includes detailed best practices for both the detection and remediation of vulnerabilities. Building on the success of the original OWASP Top Ten for web applications, OWASP has produced further OWASP is a volunteer organization that’s become a mainstay of the cybersecurity community, and their Top 10 list of app vulnerability categories is the most downloaded document on their website, the organization says.
21/08/2015 · Please visit the OWASP Top 10 project page to find the latest edition. ← Risk: 2013 Table of Contents. 2013 Top 10 List. A1-Injection → A1-Injection Injection flaws, such as SQL, OS, and LDAP injection occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing OWASP is a volunteer organization that’s become a mainstay of the cybersecurity community, and their Top 10 list of app vulnerability categories is the most downloaded document on their website, the organization says.
Owasp top 10 vulnerabilities 2013 pdf WordPress.com
Full text of "OWASP Top 10 2013.pdf (PDFy mirror)". As application security threats are constantly evolving, the current OWASP Top 10 is the 2017. This list includes detailed best practices for both the detection and remediation of vulnerabilities. Building on the success of the original OWASP Top Ten for web applications, OWASP has produced further, In 2013 OWASP completed its most recent regular three-year revision of the OWASP Top 10 Web Application Security Risks. The Top Ten list has been an important contributor to secure application development since 2004, and was further enshrined after it was included by reference in the in the Payment Card Industry Security Standards Council’s Data Security Standards, better known as the ….
Using Burp to Test for the OWASP Top Ten Burp Suite
OWASP Top 10 2013.pdf (PDFy mirror) Free Download. 21/08/2015 · Please visit the OWASP Top 10 project page to find the latest edition. ← Risk: 2013 Table of Contents. 2013 Top 10 List. A1-Injection → A1-Injection Injection flaws, such as SQL, OS, and LDAP injection occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing, Reasons for the Overhaul of the Top 10 in 2017. The OWASP Top 10 2017 is important for more than one reason. Generally, this overhaul was the need of the day, as it highlights and captures various key elements of application security particularly relevant for present-day apps..
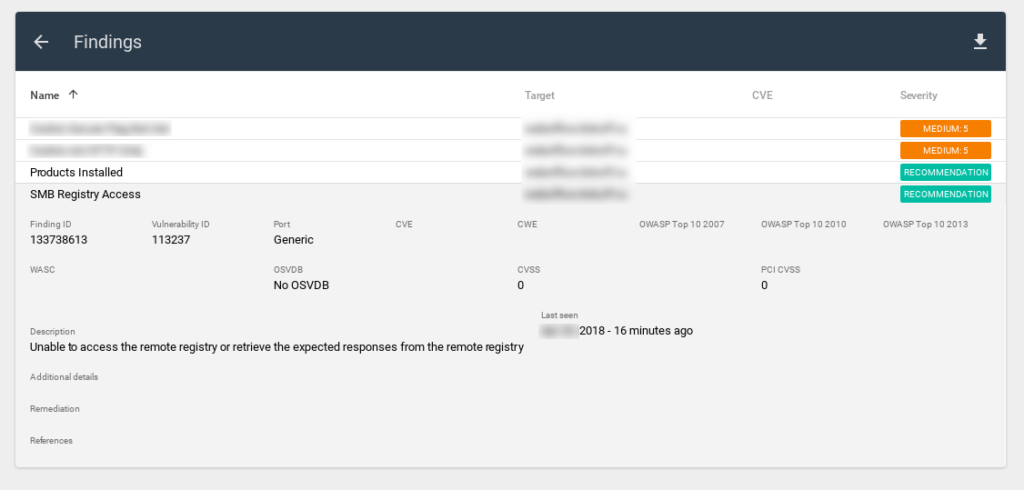
On December 14, 2015, at 4:48 PM, an OWASP Top 10 vulnerability assessment was conducted using the SAINT 8.9.28 vulnerability scanner. The scan discovered a total of one live host, and detected 19 critical 25/11/2014 · This vulnerability category is currently ranked #2 on the OWASP Top 10 chart and is very commonly exploited. These types of weaknesses …
This vulnerability, which now ranks fourth in the 2017 list, is actually a merger of two vulnerabilities from the 2013 OWASP Top 10 list: insecure direct object references and missing function level access control. Both these vulnerabilities arise as a result of improper access control. The OWASP Top 10 Project (OWASP, 2012), which assesses the most critical threat categories against web applications, places Г”Unvalidated InputГ• in the top spot, follow ed by the related XSS Flaws and
The OWASP Foundation typically publishes a list of the top 10 security threats on an annual basis (2017 being an exception where RC1 was rejected and revised based on inputs from market experts Threat Prevention Coverage – OWASP Top 10 Analysis of Check Point Coverage for OWASP Top 10 Website Vulnerability Classes The Open Web Application Security Project (OWASP) is a worldwide not-for-profit charitable organization focused on
OWASP Top 10 Presents the 10 most critical web application security risks Produced by the Open Web Application Security Project (OWASP) Available on line www.owasp.org Updated in 2013 Not Exhaustive hundreds of other issues occure in Web Security But it is foccused on the most critical ones Berner Fachhochschule j Haute cole spcialise bernoise j Berne University of Applied Sciences 10. OWASP 20/11/2018В В· On June 12, 2013 the OWASP Top 10 for 2013 was officially released. This version was updated based on numerous comments received during the comment period after the release candidate was released in Feb. 2013.
OWASP Top 10.2 While the current version was published in 2013, a new 2017 Release Candidate version is currently available for public review. The OWASP Top 10 represents a … In 2013 OWASP completed its most recent regular three-year revision of the OWASP Top 10 Web Application Security Risks. The Top Ten list has been an important contributor to secure application development since 2004, and was further enshrined after it was included by reference in the in the Payment Card Industry Security Standards Council’s Data Security Standards, better known as the …
2/02/2015В В· Sensitive Data Exposure is currently ranked #6 on the OWASP Top 10 chart. If your web applications do not properly protect sensitive data, such as credit car... Top 10 2013.pdf.Every three years the Open Source Web Application Consortium releases its list of the top 10 web vulnerabilities. Year after year, top threats like SQL injection.May 29, 2011.
ZAP proxy covers which Top 10 security vulnerabilities that OWASP has released for 2013 Showing 1-5 of 5 messages •OWASP Top 10 is a list of the most risky web app vulnerabilities •Test the devices and services against OWASP Top 10 to establish a common baseline •Low resources in the devices are not an excuse for not showing due care in security
The 2013 Top 10 list is based on data from seven application security firms, spanning over 500,000 vulnerabilities across hundreds of organizations. OWASP prioritized the top 10 according to their prevalence and their relative exploitability, detectability, and impact. •OWASP Top 10 is a list of the most risky web app vulnerabilities •Test the devices and services against OWASP Top 10 to establish a common baseline •Low resources in the devices are not an excuse for not showing due care in security
OWASP Top 10.2 While the current version was published in 2013, a new 2017 Release Candidate version is currently available for public review. The OWASP Top 10 represents a … Agenda • Introductions • Whirlwind Introduction to OWASP Top 10 2013 • Resources to help you • Quick review/intro to HTTP Proxies • Testing for Injection
On December 14, 2015, at 4:48 PM, an OWASP Top 10 vulnerability assessment was conducted using the SAINT 8.9.28 vulnerability scanner. The scan discovered a total of one live host, and detected 19 critical Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection') ParentOf Base - a weakness that is described in an abstract fashion, but with sufficient details to infer specific methods for detection and prevention.
Add Serialization Vulnerabilities to Top 10 В· Issue #92

CSRF OWASP Top 10 Vulnerabilities Treehouse. As application security threats are constantly evolving, the current OWASP Top 10 is the 2017. This list includes detailed best practices for both the detection and remediation of vulnerabilities. Building on the success of the original OWASP Top Ten for web applications, OWASP has produced further, OWASP Top 10 Presents the 10 most critical web application security risks Produced by the Open Web Application Security Project (OWASP) Available on line www.owasp.org Updated in 2013 Not Exhaustive hundreds of other issues occure in Web Security But it is foccused on the most critical ones Berner Fachhochschule j Haute cole spcialise bernoise j Berne University of Applied Sciences 10. OWASP.
Using Burp to Test for the OWASP Top Ten Burp Suite. In 2013 OWASP completed its most recent regular three-year revision of the OWASP Top 10 Web Application Security Risks. The Top Ten list has been an important contributor to secure application development since 2004, and was further enshrined after it was included by reference in the in the Payment Card Industry Security Standards Council’s Data Security Standards, better known as the …, ZAP proxy covers which Top 10 security vulnerabilities that OWASP has released for 2013 Showing 1-5 of 5 messages.
OWASP Top 10 Vulnerabilities #2 Broken YouTube
CSRF OWASP Top 10 Vulnerabilities Treehouse. •OWASP Top 10 is a list of the most risky web app vulnerabilities •Test the devices and services against OWASP Top 10 to establish a common baseline •Low resources in the devices are not an excuse for not showing due care in security https://uk.wikipedia.org/wiki/OWASP Our OWASP TOP 10 posts offer an insight into each of the 10 vulnerability types on OWASP’s list. We describe the vulnerabilities, the impact they can have, and highlight well-known examples of events involving them. Of course, we also explain how to discover these vulnerabilities, providing code.

OWASP Top 10.2 While the current version was published in 2013, a new 2017 Release Candidate version is currently available for public review. The OWASP Top 10 represents a … Im looking for if somebody has done the analysis, maybe some of the 10 are potentially at risk and the rest are safe. Or they are all safe after CRM in installed (out of the box) and then it depends on any apps or 'add-on' applications ? Any information is helpful
In 2013 OWASP completed its most recent regular three-year revision of the OWASP Top 10 Web Application Security Risks. The Top Ten list has been an important contributor to secure application development since 2004, and was further enshrined after it was included by reference in the in the Payment Card Industry Security Standards Council’s Data Security Standards, better known as the … Welcome Welcome to the OWASP Top 10 2013! This update broadens one of categories from the 2010 version to be more inclusive of common, important vulnerabilities, and reorders some of the others based on changing prevalence data.
OWASP Top 10 Vulnerabilities. Preview. Start a free Basic trial to watch this video. Sign up for Treehouse . CSRF 7:44 with Jared Smith. A CSRF attack forces a logged-on victim’s browser to send a forged HTTP request, including the victim’s session cookie and any other automatically included authentication information, to a vulnerable web application. This allows the attacker to force the OWASP Top 10 Vulnerabilities. Preview. Start a free Basic trial to watch this video. Sign up for Treehouse . CSRF 7:44 with Jared Smith. A CSRF attack forces a logged-on victim’s browser to send a forged HTTP request, including the victim’s session cookie and any other automatically included authentication information, to a vulnerable web application. This allows the attacker to force the
Our OWASP TOP 10 posts offer an insight into each of the 10 vulnerability types on OWASP’s list. We describe the vulnerabilities, the impact they can have, and highlight well-known examples of events involving them. Of course, we also explain how to discover these vulnerabilities, providing code •OWASP Top 10 is a list of the most risky web app vulnerabilities •Test the devices and services against OWASP Top 10 to establish a common baseline •Low resources in the devices are not an excuse for not showing due care in security
25/11/2014 · This vulnerability category is currently ranked #2 on the OWASP Top 10 chart and is very commonly exploited. These types of weaknesses … Reasons for the Overhaul of the Top 10 in 2017. The OWASP Top 10 2017 is important for more than one reason. Generally, this overhaul was the need of the day, as it highlights and captures various key elements of application security particularly relevant for present-day apps.
Agenda • Introductions • Whirlwind Introduction to OWASP Top 10 2013 • Resources to help you • Quick review/intro to HTTP Proxies • Testing for Injection OWASP Top 10 Presents the 10 most critical web application security risks Produced by the Open Web Application Security Project (OWASP) Available on line www.owasp.org Updated in 2013 Not Exhaustive hundreds of other issues occure in Web Security But it is foccused on the most critical ones Berner Fachhochschule j Haute cole spcialise bernoise j Berne University of Applied Sciences 10. OWASP
OWASP top ten security vulnerabilities 2013. To guide developers for what they need to protect against, the Open Web Application Security Project publishes an annual document that lists the ten most critical security vulnerabilities identified for a year. Support Center Burp Testing Methodologies Using Burp to Test for the OWASP Top Ten Using Burp to Test for the OWASP Top Ten Use the links below to discover how Burp can be used to find the vulnerabilties currently listed in the OWASP Top 10.
This open-source tool was developed at the Open Web Application Security Project (OWASP). Its main goal is to allow easy penetration testing to find vulnerabilities in web applications. It is ideal for developers and functional testers as well as security experts. This open-source tool was developed at the Open Web Application Security Project (OWASP). Its main goal is to allow easy penetration testing to find vulnerabilities in web applications. It is ideal for developers and functional testers as well as security experts.
The 2013 OWASP Top 10 release candidate is out and available for comment now. Since the list’s inception in 2004 much has changed online, and much has stayed the same. Many of the vulnerabilities from the original top ten have been on every list since or … This open-source tool was developed at the Open Web Application Security Project (OWASP). Its main goal is to allow easy penetration testing to find vulnerabilities in web applications. It is ideal for developers and functional testers as well as security experts.
OWASP Top 10.2 While the current version was published in 2013, a new 2017 Release Candidate version is currently available for public review. The OWASP Top 10 represents a … OWASP TOP 10 2013 compliance report Description The primary aim of the OWASP Top 10 is to educate developers, designers, architects, managers, and organizations
This open-source tool was developed at the Open Web Application Security Project (OWASP). Its main goal is to allow easy penetration testing to find vulnerabilities in web applications. It is ideal for developers and functional testers as well as security experts. OWASP Top 10 Security Vulnerabilities 2013 This paper addresses security vulnerabilities documented by the OWASP for the year 20132. Lucky enough, the OWASP Top 10 list for the year 2013 doesn’t differ much from lists published for previous years, except for changes in ranking. The listed security threats are probably the most severe threats and application developers to be aware of …


